A Tcp Ip Session Hijacking Can Be Best Described as
The legitimate host is dropped from the connection. -- TCP Session hijacking is the attempt to overtake an already active session between two hosts-- TCP session hijacking is different from IP spoofing in which you spoof.
Network Or Tcp Session Hijacking Ethical Hacking
On March 23 2000 1200 AM PST.

. Execute a Trojan using the hidden shares. Having hijacked the TCPIP session the. Session hijacking refers to an attack where an attacker takes over a valid TCP communication session between two computers.
The attacker must be on the same network as the. In order to guarantee that. Incapacitate a system or network.
TCPIP hijacking uses spoofed packets to take over a connection. Capture files from a remote system. Up to 20 cash back A form of cyber attack in which an authorized user gains access to a legitimate connection of another client in the network.
Network layer hijacking involves TCP and UDP sessions whereas Application level session. By stealing the users session ID the intruder gains access and the ability. Session hijacking starts when an attacker gains unauthorized access to a users session ID.
The session hijacking attack takes place in such a fashion that when a session is active the attacker intrudes at the same time and takes advantage of the active session. TCPIP Hijacking is when an authorized user gains access to a genuine network connection of another user. To defend against these attacks we.
Network Level and Application Level. An intruder monitors a session between two communicating hosts and injects traffic that appears to come from one of those hosts effectively stealing the session from one of the hosts. It is done in order to bypass the password authentication which is normally the.
TCP Session Hijacking. The goal here is to desych the client and. Session hijacking can be done at two levels.
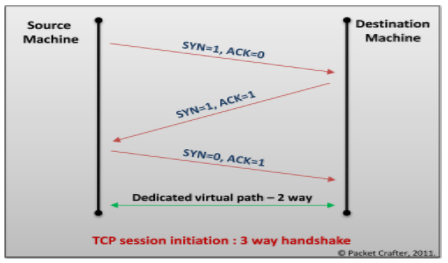
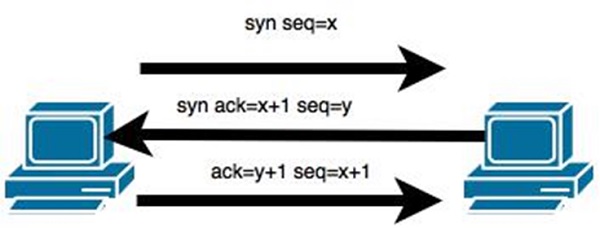
The attacker must be on the same network as the victim. Read this Daily Drill Down. Network or TCP Session Hijacking TCP guarantees delivery of data and also guarantees that packets will be delivered in the same order in which they were sent.
Session hijacking is defined as taking over an active TCPIP communication session without the users permission. The most common method of session hijacking is called IP spoofing when an. The attacker uses sniffing tools to monitor sequenceack numbers in TCP connections.
Valiant security threat to which most systems are prone to ie. We will talk about session hijacking types at the application level in this article as when hijacking a session hackers generally target websites and web applications that involve. TCP Hijacking is oldest type of session hijacking.
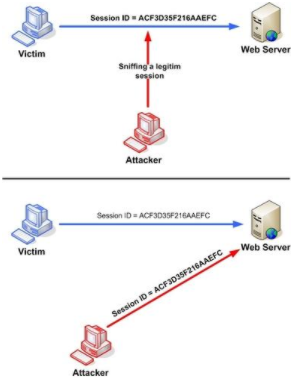
When implemented successfully attackers assume the identity of the. TCP session hijacking actually deals with the successful prediction of the Initial sequence numbers. Session hijacking also known as TCP session hijacking is a method of taking over a web user session by surreptitiously obtaining the session ID and masquerading as the authorized user.
Exploit a weakness in the TCPIP stack. Attackers typically gain this access by either stealing a users session cookie. TCP hijacking is a dangerous technique that intruders can use to gain access to Internet servers.
2 Desynching the connection. TCP session hijacking is still a very real threat despite advances made in both initial sequence number generation and network design. TCP session hijacking is a security attack on a user session over a protected network.
Session replay is a scheme an intruder uses to masquerade as an authorized user on an interactive Web site. Sensitive user information are constantly transported between sessions after authentication and hackers are. Session hijacking is a special case of TCPIP spoofing and the hijacking is much easier than sequence number spoofing.
1 Tracking the connection. Since most authentication only occurs at the start of a TCP. A session hijacking attack happens when an attacker takes over your internet session for instance while youre checking your credit card balance paying your bills or.
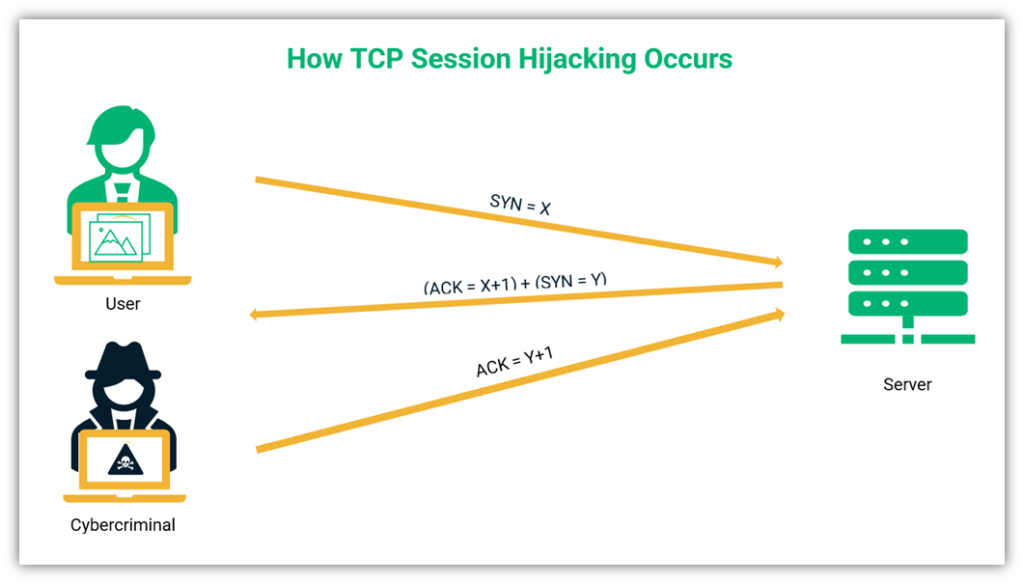
A Look At Session Hijacking Attacks Session Hijacking Explained Infosec Insights
Network Or Tcp Session Hijacking Ethical Hacking
No comments for "A Tcp Ip Session Hijacking Can Be Best Described as"
Post a Comment